As online privacy and security become increasingly crucial, online privacy and security continues to grow. It’s vital to grasp the technology that shields our footprint. A key player in this realm is the server, a fundamental tool that shields users IP addresses and bolsters security. This piece seeks to shed light on the role of a server, its operational mechanics and the different varieties out there. By delving into these aspects, you’ll gain an insight into how proxy servers can fortify your online safety and privacy.
What is a proxy server?
A proxy server functions as a middleman between users and the internet serving as a barrier for private networks, against cyber threats. Referred to as an “intermediary ” it sits between end users and the sites they access.
When a computer goes online it gets given an IP address like how a house has a street address. This special IP address helps guide data to where it needs to go and tags outgoing data with a return address for verification by other gadgets. A proxy server acts like another computer, on the internet having its unique IP address.
How does a proxy server work?
A proxy server works by receiving your web requests and forwarding them to the destination server. Here’s a step-by-step breakdown of how a proxy server operates:
- Request: You start by requesting to open a webpage using your internet browser.
- Forwarding: The proxy server receives the request. Then passes it along, to the target server.
- Response: The server being targeted handles the request. Then returns the requested information to the proxy server.
- Delivery: The intermediary server gets the information. Sends it over to your web browser.
When you use a server it hides your IP address adding a layer of security and anonymity, to your online actions.
Types of Proxy Servers
Different kinds of servers are available each, with its own specific functions and levels of anonymity, security and efficiency. Knowing about these variations can assist you in selecting the proxy server for your requirements. Here are some of the types of proxy servers:
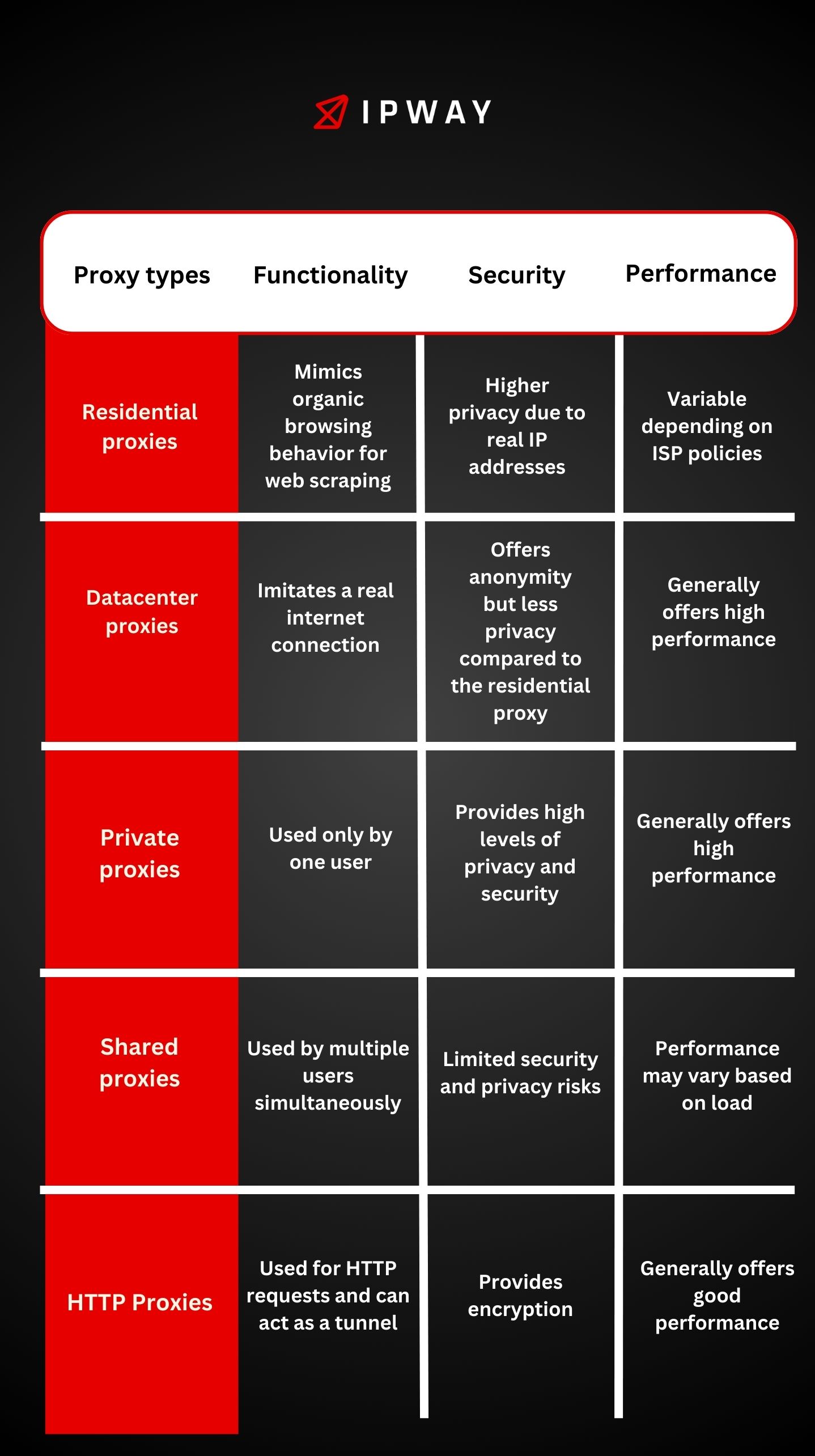
Datacenter Proxies
Datacenter proxies are separate from Internet Service Providers (ISPs) as they come from data centers, which’re facilities with many servers. These proxies are valued for their quickness and affordability. They are commonly employed for tasks like web scraping, accessing restricted content and handling online operations. Nonetheless due to their detectability and susceptibility to website blocks they are not the choice, for activities that demand top tier anonymity.
Residential Proxies
Residential proxies utilize IP addresses that are allocated by internet service providers to individuals who own homes. These proxies redirect your activity through authentic residential IP addresses giving the impression that you are a regular user to websites. Residential proxies are known for their reliability and are more challenging to identify than datacenter proxies making them perfect for activities such, as handling numerous social media profiles circumventing geographic restrictions and performing market analysis.
ISP Proxies
ISP proxies bring together the advantages of datacenter and residential proxies by leveraging datacenter infrastructure paired with IP addresses from ISPs. This unique blend combines the speed and dependability of datacenter proxies with the authenticity and reduced visibility of proxies. ISP proxies are ideal for tasks that demand a balance of efficiency and anonymity such, as research and automated online operations.
Mobile Proxies
Mobile proxies utilize IP addresses provided by mobile service providers. These proxies offer an advantage as they can switch between various IP addresses as mobile devices shift and reconnect to different cell towers. This dynamic rotation ensures a level of anonymity making mobile proxies well suited for activities that demand frequent IP changes, such, as ad validation, social media account management and accessing content tailored for mobile platforms.
Transparent Proxy
A see through proxy, also referred to as an inline or intercepting proxy does not conceal your IP address when you browse websites. Its main purpose is to store websites to speed up access and screen content using standards. Transparent proxies are commonly utilized by companies and internet service providers (ISPs) to enhance network efficiency and uphold internet usage regulations. Nonetheless they do not provide privacy or anonymity.
Anonymous Proxy
When you use a proxy it conceals your IP address from the websites you browse but indicates that you are employing a proxy service. This kind of proxy offers a degree of anonymity and is frequently utilized to circumvent geographical limitations reach restricted content and uphold a certain level of privacy when surfing the web. Anonymous proxies are ideal, for individuals looking to conceal their IP address without concealing their utilization of a proxy server.
High Anonimity Proxy
Elite proxies, also referred to high anonymity proxies provide top tier anonymity. These proxies not conceal your IP address but also ensure that your usage of a proxy server remains undisclosed. This heightened level of anonymity makes it challenging for websites to monitor your behavior or recognize that you are utilizing a proxy. Elite proxies are particularly suitable, for safeguarding online tasks like secure browsing, private communications and activities that demand utmost privacy.
Public Proxy
Free public proxies are accessible to all users without any authentication. These proxies can be found on proxy server listings and are generally slow, unreliable and carry potential security threats. Due to their vulnerability, to misuse and cyber attacks they are not recommended for tasks that demand levels of security or anonymity. Public proxies are commonly utilized for internet browsing and testing activities.
Shared Proxies
Shared proxies are utilized by users at the same time. These proxies offer a budget friendly option compared to private proxies since the expenses are divided among multiple users. Nonetheless due to their shared nature they might operate at a pace and provide lower security levels. Shared proxies work well for online tasks that do not require high speeds and top notch privacy protection, such, as casual browsing and simple data gathering.
Rotating Proxies
Rotating proxies automatically switch your IP address regularly or after every request. This consistent rotation offers a level of privacy and lowers the chances of being identified or blocked by websites. Rotating proxies are well suited for tasks like web scraping, data mining and other automated activities that need access to substantial data, without setting off security alerts.
Reverse Proxy
A reverse proxy sits in front of web servers. Directs client requests to the right backend server. This kind of proxy boosts security distributes load and stores data for websites. Reverse proxies aid in spreading workload, across servers guarding against DDoS attacks and storing content to boost website performance. They are frequently employed by websites and online platforms to handle traffic and guarantee seamless user interactions.
How to get a proxy
Getting a proxy server can be done in ways each, with its own benefits and factors to consider. Depending on what you require your budget and technical skills you have the option of using proxy services paid proxy services or setting up your personal proxy server. Here’s a detailed look at each method:
Free Proxy Services
There are free proxy services out there that offer an easy way for users to try out proxies without having to pay anything upfront.. These services usually have some restrictions and possible dangers.
Advantages
- Cost-free: Free proxy services as their name implies do not necessitate any commitment, which makes them appealing to individuals who use them occasionally or are working with limited funds.
- Ease of Use: You can usually use proxies with ease usually just needing a basic setup, in your web browser or app.
Disadvantages
- Limited Reliability: Free proxy servers tend to be slower and less dependable because they experience usage and have limited infrastructure.
- Security Risks: Some of these proxies might not have security features leaving them open to cyber threats and privacy breaches. Moreover certain free proxy services could track your actions and share them with outside organizations.
- Performance Issues: Using proxies often leads to delays and frequent interruptions, which can significantly impact your browsing experience.
Paid Proxy Services
Paid proxy services provide a level of dependability, velocity and protection in contrast to complimentary proxies. These services accommodate the requirements of users as well, as businesses by offering customized solutions to address particular needs.
Advantages
- High Performance: Using paid proxies can provide speeds improved uptime and more reliable connections, which are ideal, for handling tasks that require a lot of data.
- Enhanced Security: Typically these services come with high level security options, like SSL encryption authentication methods and frequent updates to prevent vulnerabilities.
- Customer support: Paid proxy services come with customer assistance to help you with setup problem solving and personalization ensuring an user experience.
- Variety of Options: Various paid services provide a range of options, such, as residential, datacenter, mobile and rotating proxies tailored to meet different needs.
Disadvantages
- Cost: The main downside is the expense as it can differ greatly depending on the kind and amount of proxies needed. Nonetheless the cost is usually justified by the improved performance and security it provides.
How does the proxy protect computer privacy and data?
A proxy server acts as a dual purpose shield serving both as a firewall and a filter. Users or network administrators can customize its settings to safeguard data and privacy. By scrutinizing the outgoing data on your device or network the proxy server enforces rules that shield your digital identity from exposure to external entities.
This setup ensures that only the proxy’s IP address is visible to threats, like hackers preventing them from directly reaching your personal information, schedules, apps or files.
When you use a server your requests go through the proxy first and then it retrieves the information you need from the internet. If the proxy server has encryption capabilities it provides a safeguard, for passwords and other confidential information.
Do proxies hide your IP?
Certainly proxies are effective in concealing your IP address, which is their main purpose. Yet it’s crucial to recognize that proxies serve other functions beyond just hiding ones IP address. They can help bypass geo restrictions, filter or extract web content. Offer additional functionalities.
Further details about these applications can be found in parts of this article. Additionally it’s important to mention that while maintaining anonymity is essential for individuals seeking privacy businesses often utilize proxies, for specialized and intricate tasks.
Is VPN the same as proxy?
Certainly proxies indeed conceal your IP address and often that is their main purpose. Nevertheless it’s crucial to recognize that proxies serve other functions beyond just hiding the users original IP address. These additional purposes include circumventing geo restrictions, managing or extracting web content and so forth.
You can delve deeper into these uses in parts of this article. Additionally it’s important to mention that while maintaining anonymity is frequently essential for individuals seeking privacy businesses typically employ proxies, for specialized and intricate tasks.
Which is better – VPN or proxy?
Web proxies and VPNs each have their benefits and the decision on which to use depends on the specific task. Proxies are known for their efficiency in handling, fetching and processing data volumes. They are more economical per gigabyte of data. Provide faster connection speeds, than virtual private networks.

On the hand virtual private networks (VPNs) are typically more suitable for extensive use and improved privacy. VPNs encrypt all information, not just the data from a specific application to prevent any unnecessary leakage of data to the server. High quality VPN services also allow users to carry out tasks without experiencing delays or reduced speed ensuring strong security, alongside efficient performance.
Conclusion
To boost your privacy and security it’s crucial to grasp the role and operation of a proxy server. These servers serve as go betweens concealing your IP address and offering varying degrees of anonymity and protection depending on their type. Whether you seek a proxy for use web scraping or business endeavors being familiar with the diverse types and their functions can aid in selecting the most suitable choice for your requirements.
Furthermore comprehending the distinctions, between servers and VPNs can assist you in making well informed decisions regarding your online security strategy.
Discover how IPWAY’s innovative solutions can revolutionize your web scraping experience for a better and more efficient approach.