Tunnels are a great method of getting to your destination fast and crossing terrain that would otherwise be impossible. Whether you cross a bridge or take the subway, getting from point A to point B fast and efficiently is the final goal.
Such things are also present in networking. Surprisingly or not, online tunneling is very similar to our physical world. So, let’s dive into it and explain how tunneling works in networking, and see what is a GRE tunnel.
What is tunneling?
Just as the real, physical world uses tunnels to cross obstacles and difficult terrain, so do networks with something named tunneling.
In the world of the Internet, tunneling is a way of transporting data from one network to another. This method successfully sends data using protocols that are not supported by that network.
More specifically, it allows private network communications to be sent across public networks (i.e the Internet). Tunneling can have several advantages. For example, it ensures the security of the data transmission, enables cross-protocol compatibility, and sometimes it can be used by bypass firewalls as well.
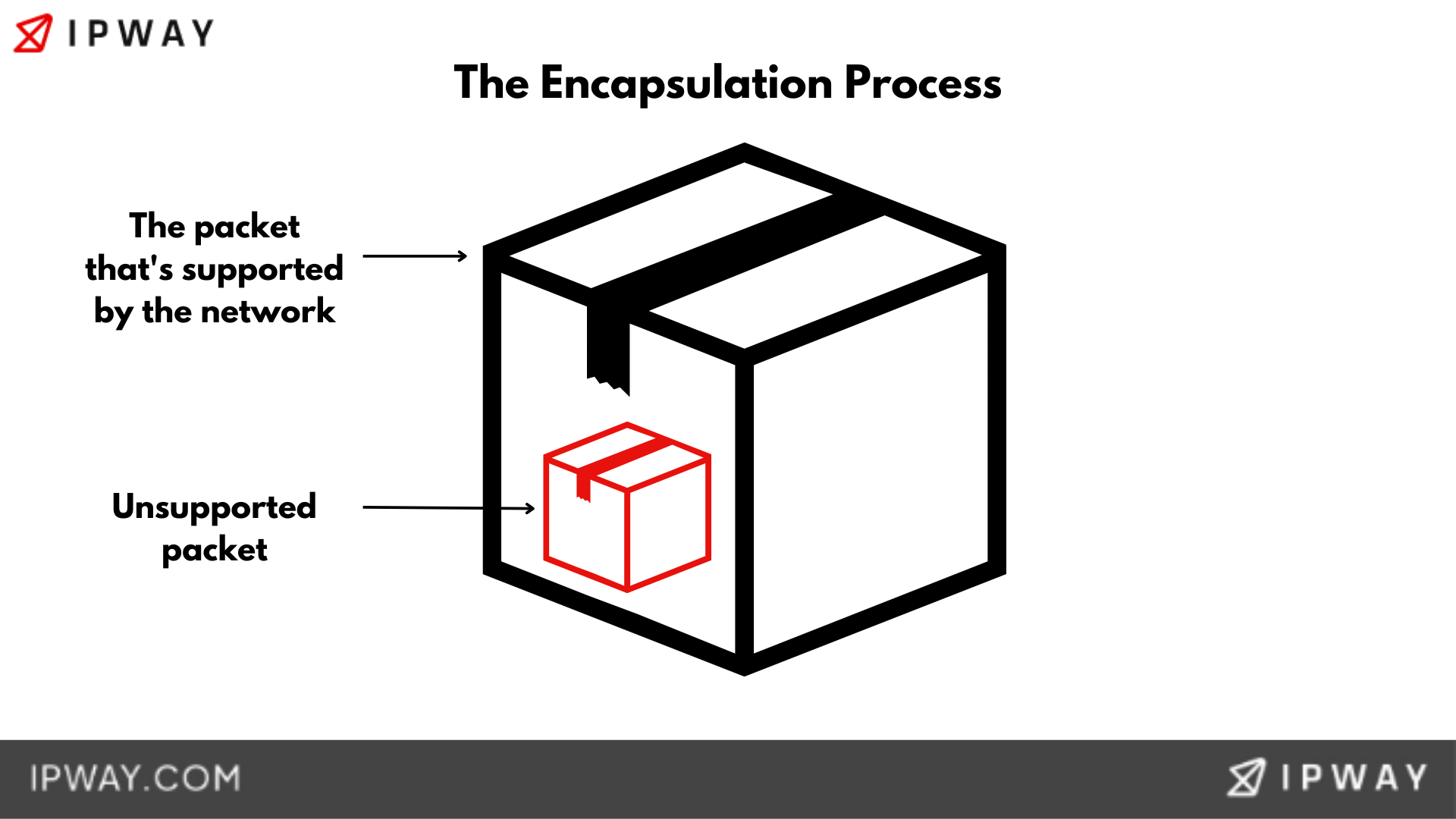
This is achieved thanks to a process called encapsulation. The latter refers to wrapping data packets inside other data packets.
In networking, a packet is a small piece of data that is re-assembled when it reaches its destination. The data packet has an IP header attached to it, and you can think of the header as the destination written on an envelope that contains a letter with specific instructions. When it reaches the destination, the packet is reassembled and the information is successfully obtained.
How does tunneling work?
In tunneling, data is broken into packets. A packet has two components: the header indicating the destination (the envelope we talked about earlier), and the payload, the packet’s actual contents.
The packets are then encrypted and, as they travel through the tunnel, encapsulation takes place. This encapsulation is pretty much a packet inside another packet. Here, the header and payload of the original packet are placed inside the payload bit of the surrounding packet.
The result is that the inside packet itself will become the payload. The easiest way to think of this is of a box placed inside another box.
The most common tunneling scenario revolves around private network data and protocol information being wrapped in public network units/packets.
Because private data is now ‘disguised’ as public information, it is able to travel across the Internet. Encapsulation allows packets to reach their destination successfully. When they arrive where they’re supposed to, the packets are de-capsulated, decrypted, and reassembled.
Why is encapsulation useful?
If you think about it, encapsulation bears similarities with the real, physical world.
Cross-protocol compatibility
Exchanging information over the Internet is not a cakewalk. All packets traveling far and wide across networks use networking protocols. The thing is, not all protocols go hand in hand with all networks.
Let’s put it like this. If you wanted to send IPv6 packets across a network that supports only IPv4, you would need to encapsulate the IPv6 information inside IPv4 packets. This disguise ensures that the packets based on the latest version of the Internet Protocol can be transmitted across an IPv4 – based network.
Helping encrypted data reach its destination safely
Encapsulation helps in making sure the core data inside the ‘envelope’ cannot be altered or intercepted. How is that? Let’s explain.
Encryption is a great method of bolstering data integrity and security. That’s because the data can only be decrypted and ‘read’ with a secret, specific encryption key.
This is super useful for packets, including their IP headers, right? But if the entire box is sealed and the address is scrambled, how will the postman (a router) be able to send it to its destination?
Here comes encapsulation. It wraps the encrypted packet inside a decrypted packet (the sealed box is placed in another box containing the address). In doing so, the packet can travel across the Internet normally and reach its destination safely and sound.
With this in mind, we can say that tunneling and encapsulation help private data travel across the World Wide Web without being tampered with.
What is a GRE tunnel?
Tunneling works based on different protocols. One of them is the GRE protocol. Short for Generic Routing Encapsulation, it takes data packets that use one routing protocol and encapsulates them inside the packets of another protocol.
A GRE tunnel helps packets use protocols that are not supported by all networks. It’s the compatibility we discussed earlier, as it helps data travel across the web and reach its destination successfully.
The process resembles traveling to another country by plane. A person has to arrive at their specific destination. But the destination itself cannot be reached by other means than flying. Once the plane reaches the airport and lands, the person will then be able to reach their destination.
To put it simply, the impassable route is the network that supports only certain routing protocols. The person and the plane are the data packets. The person (the unsupported protocol) takes the plane (the supported protocol), to be able to reach the destination.
How does GRE tunneling work?
GRE tunneling is usually configured between two routers. They each act as one end of the tunnel configured to send and receive GRE packets directly. It’s as simple as connecting Point A to Point B.
Now, in between these points, there can also be other additional routers. However, these ones will not open the encapsulated packets (they won’t open the envelope containing the letter). They will only read the headers on the outer layer of the encapsulated packets (the address written on the envelope) to know where to forward them.
A GRE tunnel itself is like a walkway or a bridge above a busy road. You cannot really dodge all the incoming traffic, as the road was built for cars, not pedestrians. What you can do, instead, is use the walkway (the GRE tunnel) to get from one side of the curb to another.
How does GRE encapsulation work?
We already saw that all data sent over a network is split into packets that have two components: the header and the payload.
The payload is the envelope’s contents, the letter. The header is the writing on the envelope (sender, receiver, etc.). Each network protocol will attach a header to each packet in the encapsulation process.
For this, GRE attaches two headers to each packet: the GRE header itself, as well as the IP header. Let’s see what each of them does.
- The GRE header shows the network protocol used by the original, encapsulated packet.
- The IP header wraps around the original packet’s header and payload.
The result is that GRE packets usually have two IP headers; one for the original packet (the sealed box), and the other added by the GRE protocol.
And in all the wrapping and packaging, only the routers at each end of the GRE tunnel will be able to read the original, non-GRE IP header that’s attached to the inside packet.
Does a GRE tunnel have any disadvantages?
The simple answer is yes. It has to do with speed and transfer times. Let’s elaborate on that.
In networking, there are standards that measure and limit how large data packets can be as they travel across networks. It’s similar to the weight limit for vehicles passing on bridges.
We showed earlier that GRE tunneling adds two extra headers to each packet. This means a few more bytes to the packet’s size. This translates as adding more weight to them. If the packet’s size exceeds the limits set by those standards, it will be fragmented.
Fragmentation means the packet will be further broken into smaller pieces, hence more things to be delivered as fast as possible. Fragmentation slows down packet delivery as it takes more time to receive them all before re-assembling them.
Furthermore, because the packet is split into even smaller bits, more computer power will be needed for the processes of breaking down and reassembling too many packets.
There is still some sort of compromise. Even though data transfer is delayed, GRE can help packets take faster network paths (encapsulation helps avoid protocol incompatibility), which in turn could make up for the lost time.
Conclusion
A GRE tunnel is an ingenious way of making sure data reaches its destination by traveling over networks that otherwise would have simply been incompatible.
Even though it has minor disadvantages, GRE tunneling is the networking equivalent of walkways, and any other shortcut that helps you say, avoid traffic or get from Point A to Point B.
Encapsulation is a core component of the entire tunneling process. This is basically the Trojan horse that travels from one network to another. The unsupported protocol is wrapped around a protocol that’s supported by the target network. In doing so, companies can send data over IPv4 and IPv6-based networks, irrespective of which version is used.
Through tunneling and encapsulation, data will travel safely and efficiently, even if it might have to be further broken down into smaller bits because of the GRE protocol. It will make up for the lost speed by finding the best route and crossing over networks that would have been inaccessible otherwise.
