In the digital environment we’re in today where privacy issues and data handling are hot topics, in the tech world proxies have become crucial for managing and safeguarding network traffic. Transparent proxies stand out among the proxy types because they can work discreetly without users noticing or requiring manual setup from the users end.
What is a Transparent Proxy and How Does It Work?
In today’s digital landscape, where privacy concerns and data management are at the forefront of technological discussions, proxies have emerged as essential tools for managing and securing network traffic. Among the various types of proxies, transparent proxies hold a unique position due to their ability to operate without the user’s awareness or the need for manual configuration on the client-side. This article provides a comprehensive guide to transparent proxies, covering how they work, their use cases, the pros and cons, and methods for detecting their presence.
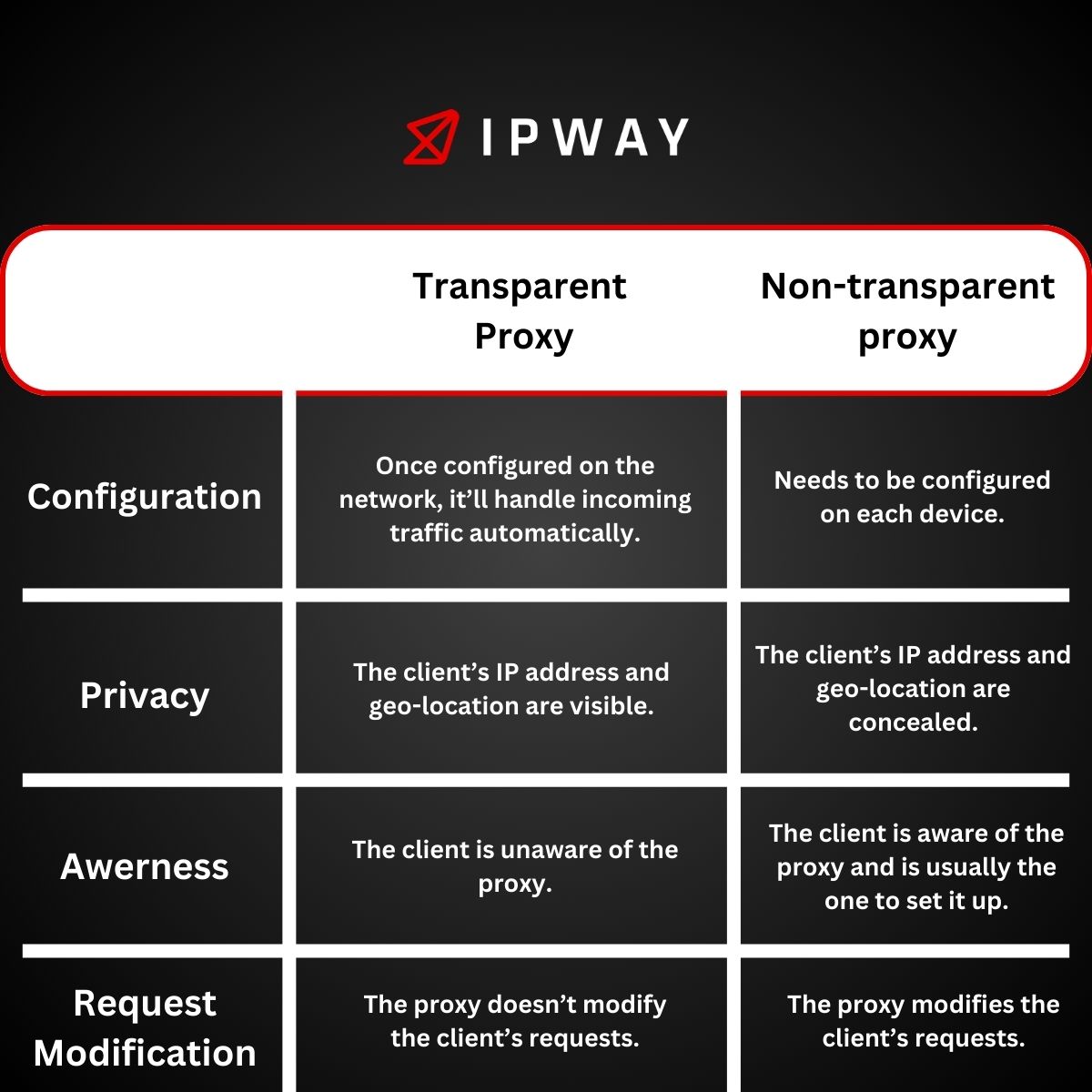
How Does a Transparent Proxy Work?
Sometimes called an inline proxy or a see through proxy a proxy works by intercepting user requests without changing how users interact with the internet. Unlike proxies that usually need users to set up their browsers or devices, transparent proxies operate seamlessly without any input, from users. This hidden functionality is why it is known as a proxy, as it operates discreetly without the users knowledge.
The Mechanism of a Transparent Proxy
To grasp the functioning of a proxy server effectively it is crucial to dissect the process into various essential stages:
- Request Interception: When someone tries to access a website on their device and sends a request via HTTP or HTTPS to the server where the site is located if there is a proxy in use the request gets intercepted before reaching its final destination. This interception usually happens at a network gateway, like a router or firewall where the proxy is set up to capture all traffic automatically.
- Processing the Request: After the proxy catches the request it handles the data based on set rules. This handling could involve screening content restricting entry to websites, recording user actions or storing often visited pages for faster access later on. At times the proxy may also alter the request. Insert extra details, like login tokens or tracking identifiers.
- Forwarding the Request: After the proxy catches the request it handles the data based on set rules. This handling could involve screening content restricting entry to websites, recording user actions or storing often visited pages for faster access later on. At times the proxy may also alter the request. Insert extra details, like login tokens or tracking identifiers.
- Returning the Response: The proxy server receives the response from the server. May process it if needed (such as caching the content or inserting ads) before sending it back to the users device seamlessly without any noticeable changes, in operation.
- Seamless User Experience: The user won’t encounter any disruptions or obvious alterations to their browsing experience during this process. The proxys activities remain concealed and to the user everything seems normal as they interact with the internet.
Types of Transparent Proxies
There are types of clear proxies available, for different purposes:
- Caching Transparent Proxies: These proxy servers are created to store accessed web content for faster retrieval purposes and reduced bandwidth consumption by users, in a corporate setting where multiple individuals access identical resources.
- Content Filtering Proxies: Content filtering proxies are commonly employed in institutions and office settings to restrict access to certain types of content by blocking websites based on categories and keywords or specific URLs to prevent users from viewing restricted materials—a practice that helps uphold compliance, with internet usage rules.
- Load Balancing Proxies: Load balancer proxies help spread out network traffic among servers to improve efficiency and prevent any one server from being overloaded with requests, which is crucial for maintaining top performance and reliability, in data centers and extensive web applications.
- Ad Injection Proxies: Certain types of proxies are utilized to insert advertisements into web pages while they are being loaded online.This method is frequently utilized by ISPs or public Wi Fi providers who provide internet access in return, for showcasing ads to users.Although this approach can bring in revenue it is typically considered invasive by users.
- SSL Interception Proxies: These proxies intercept and decrypt SSL/TLS traffic to help administrators examine and filter encrypted data effectively for security threats detection and prevention, within encrypted communications networks; however it is crucial to handle SSL interception proxies to protect user privacy and trust.
Transparent Proxy Use Cases
Transparent proxies are utilized in situations because they can function without requiring user input or interaction Here are a few typical scenarios where they are commonly used:
Content Filtering and Censorship:
Transparent proxies are frequently utilized for content filtering purposes by institutions as well as libraries and businesses alike to regulate access to certain types of websites, like those featuring adult content or social media platforms and online gaming sites. This practice allows these entities to uphold their usage guidelines effectively while ensuring that network resources are utilized in a manner.
Governments may also employ proxies for censorship objectives in regions where internet access is tightly controlled. These proxies can restrict access to politically sensitive material or sites that question the current state of affairs, within the country by filtering traffic according to keywords or URLs.
Traffic Monitoring and Logging:
Transparent proxies serve as tools for monitoring and recording network traffic activities efficiently in various settings such as businesses or organizations. These proxies play a role in overseeing employee internet browsing habits to enforce company guidelines effectively and ensure compliance. To illustrate this point further—a transparent proxy has the capability to record details like the websites visited by employees along, with the time spent per visit and the specific content accessed during their sessions..
This information has applications: for instance, adhering to regulations efficiently or identifying internal risks are some practical uses of this data analysis tool in place. Moreover in settings like schools and public establishments network monitoring with transparent proxies can safeguard users, against harmful or unsuitable online materials.
Caching:
Transparent proxies also play a role in caching content effectively on the internet world today by saving duplicates of popular web pages accessed frequently by users to minimize the bandwidth needed for fetching the identical data repeatedly across networks or organizations, like a shared online library or resources being accessed repeatedly by various users.
Not just enhancing user experience through faster loading times. Also aiding organizations in better bandwidth utilization. Especially in areas, with slow internet or expensive data plans.
Ad Insertion:
Some providers employ transparent proxies to integrate ads into the websites users browse on the internet. This method is often seen in public Wi Fi networks where users receive internet access in return for viewing advertisements. The transparent proxy intercepts requests and adjusts the content, by adding ads before presenting it to the user.
This model has the potential to generate revenue for service providers; however it faces pushback from users who feel that the advertisements are intrusive or have worries, about the privacy implications of these changes.
Authentication and Security:
In environments and networks alike transparent proxies are utilized to enforce authentication protocols. For instance users may be prompted to log in with their credentials through a proxy before gaining internet access. This practice guarantees that network access is restricted to authorized individuals while also recording and associating all activities with users.
When it comes to security measures for networks transparent proxies play a role, in safeguard against malicious activities by screening out harmful content blocking potential phishing sites and keeping an eye out for any suspicious behavior. Through real time traffic inspection these proxies are able to identify and address threats proactively before they impact the users device.
Load Balancing:
Transparent proxies can also come in for balancing loads in environments with high traffic volume. They help spread incoming traffic among various servers to prevent any single server from getting overwhelmed and slowing down the networks performance and dependability as a whole. Especially beneficial, in data centers and cloud settings where continuous availability is of utmost importance.
Advantages and Disadvantages of Transparent Proxies
Like any other technology out there transparent proxies have both pros and cons. Knowing these can assist organizations in determining whether a transparent proxy is the fit, for their requirements.
Advantages
Seamless User Experience: One major benefit of using proxies is that they can be implemented without needing any setup or input from the user which simplifies deployment and management tasks. Especially, in situations involving non tech savvy individuals.
Centralized Control: Transparent proxies offer network administrators a way to manage internet traffic from a location which proves useful in big organizations that require consistent enforcement of policies across the board. Administrators have the ability to establish regulations for content filtering and bandwidth allocation well as security measures that are enforced on all users to maintain a uniform and compliant usage throughout the network.
Enhanced Security: By monitoring and examining network traffic flow using transparent proxies can bolster the security of a network system significantly. For instance, these proxies have the capability to restrict entry to identified websites, thereby stopping users from unknowingly downloading malware or becoming targets of phishing schemes. Moreover, they can also keep an eye out for traffic behaviors that could signal a potential breach in security. Enabling administrators to promptly address any possible threats.
Bandwidth Optimization: By using caching techniques on proxies helps in cutting down the bandwidth needed to deliver commonly viewed content efficiently which can save costs significantly especially in places with restricted bandwidth or expensive data rates. Moreover optimizing how bandwidth is utilized by these proxies can enhance the networks performance overall leading to loading times and a more pleasant user experience.
Regulatory Compliance: In fields like finance or healthcare, industries have rigorous rules on how data gets used and spread online Transparent proxies can assist companies in meeting these regulations by applying content filtering tracking user actions and making sure only authorized individuals can view confidential details
Disadvantages
Privacy Concerns: The clear visibility of these servers can spark important privacy worries for users because they might not realize that their online activities are being watched and scrutinized without their knowledge or consent – leading to feelings of privacy intrusion especially, in situations where personal or confidential data is sent over the internet.
Additionally the logging functionalities of see through proxies enable the retention of logs detailing user actions that could be archived and potentially retrieved by unauthorized individuals. Such practices can lead to security weaknesses with regards, to data breaches or improper use of data.
Performance Overhead: Using proxies can enhance network efficiency by caching data and balancing loads; however they may also cause performance issues due, to the need to intercept traffic and analyze it. This interception process can introduce delays in responding to user requests during periods of high network activity.. Consequently this might lead to loading times and a less optimal user experience especially when there are intricate filtering rules or extensive logging involved.
Limited User Control: Users may feel frustrated by the lack of control over how their data’s managed since transparent proxies function independently of user input and preferences. Users who value privacy or want control, over their security may find this particularly troubling. One scenario is when a user is unaware that their data is being rerouted through a server and as a result may not take necessary precautions like using a VPN or encrypting sensitive information.
Potential for Misuse: At times transparent proxies might be utilized for intents. For instance a proxy could be set up to insert ads reroute users to deceptive sites or gather personal data without the users approval. This misuse can lead to consequences, for security and user confidence especially when the proxy is managed by an untrustworthy or unethical party.
SSL/TLS Interception Issues: When transparent proxies conduct SSL/TLS interception without oversight and control measures in place. There could be security vulnerabilities at play here! These proxies have the power, to decrypt. Scrutinize encrypted data traffic which can potentially unveil confidential details or compromise the security of the connection itself! Moreover, users might face browser warnings in case the proxy setup isn’t spot on which could result in trust issues and service interruptions.
How to Detect a Transparent Proxy?
Identifying a proxy presents difficulties due to its elusive characteristics. Nevertheless, there are various techniques that individuals and system administrators can utilize to determine if a transparent proxy is being utilized.
IP Address Mismatch: One easy method to uncover a proxy is by examining if the IP addresses match up correctly or not when a users device communicates with a websites server during the request process. Users can cross check their IP address with the one logged by the websites server by visiting websites like whatismyip.com. If theres a difference, between the two IP addresses detected during this comparison task it’s probable that a transparent proxy has intercepted the request and transmitted it using an IP address.
Traceroute Analysis: Using the traceroute command can reveal the network path that data packets travel from the users device to the destination server step by step. It shows every stop along the way with the IP addresses of routers or proxies in between. If theres a surprise stop or an IP address that doesn’t fit the route is detected in the path taken by data packets during tracing process; it may suggest there’s a transparent proxy, in play.
To perform a traceroute test on your computer; 1. Open the command prompt in Windows. Terminal, in macOS/Linux. 2. Type either tracert [website]. Traceroute [website] substituting [website] 3. The results will display the route taken by the data packets for users to spot any irregularities.
HTTP Header Inspection: Transparent proxies might alter HTTP headers by adding them to requests or even removing them altogether without the users knowledge. To check the HTTP headers in their requests, for any changes like the presence of headers such as X, forwarded for or via users can use browser developer tools or visit websites like httpbin.org. These changes could indicate the involvement of a proxy, in the network communication.
DNS Leak Tests: When using a proxy server it can also intercept and redirect Domain Name System (DNS ) requests that help convert domain names (such as google.com ) into IP addresses. If a proxy server intercepts DNS queries it might substitute your DNS resolver, with its own.
How to Perform a DNS Leak Test:
- Visit a website such, as dnsleaktest.com or ipleak.net to conduct a DNS leak test.
- These tools can show you the DNS servers your connection is currently utilizing. If you’ve set up a DNS service, like Googles or Cloudflares 0ne point one point one but the findings indicate other DNS servers there might be a chance that a transparent proxy is rerouting your DNS requests to its own resolver.
When a proxy intercept DNS requests and a DNS leak test is done to check if your queries are being sent through DNS servers.
Conclusion
Transparent proxies are an asset for companies seeking to oversee web traffic flow and enhance content delivery while upholding internet guidelines effectively and, without user detection.They offer control over online activities but raise privacy and security issues that necessitate a clear understanding of their functions and identification methods.
Simply put Transparent proxies have their benefits across situations but need to be implemented carefully to safeguard user privacy and security concerns in mind. Whether you oversee a business network or have an interest, in managing internet traffic flow efficiently comprehending the mechanics behind transparent proxies will empower you to make well thought out choices regarding their implementation.
Discover how IPWAY’s innovative solutions can revolutionize your experience for a better and more efficient approach.
