In the realm of networking having a grasp of Internet Protocol (IP) fundamentals is essential. IPv4 emerges as the fundamental protocol, among the array of IP versions facilitating the bulk of internet communication in present times. This piece will explore the intricacies of IPv4 its structure, operational mechanisms, advantages, obstacles and security considerations.
What is IPv4?
IPv4, known as Internet Protocol version 4 is the version of the Internet Protocol (IP) that has been widely used. It was outlined in RFC 791. Serves as a system for identifying and locating computers on networks while directing traffic over the internet. The primary purpose of IPv4 is to facilitate internetworking, which’s crucial, for the functioning of the internet.
Anatomy of IPv4 Addresses
IPv4 addresses play a role in networking by offering distinct labels that enable devices to interact online. It is vital to grasp the format and elements of IPv4 addresses along with the significance of subnet masks, in assigning addresses for network administration. Below, we explore these aspects in detail:
Structure of IPv4 Address
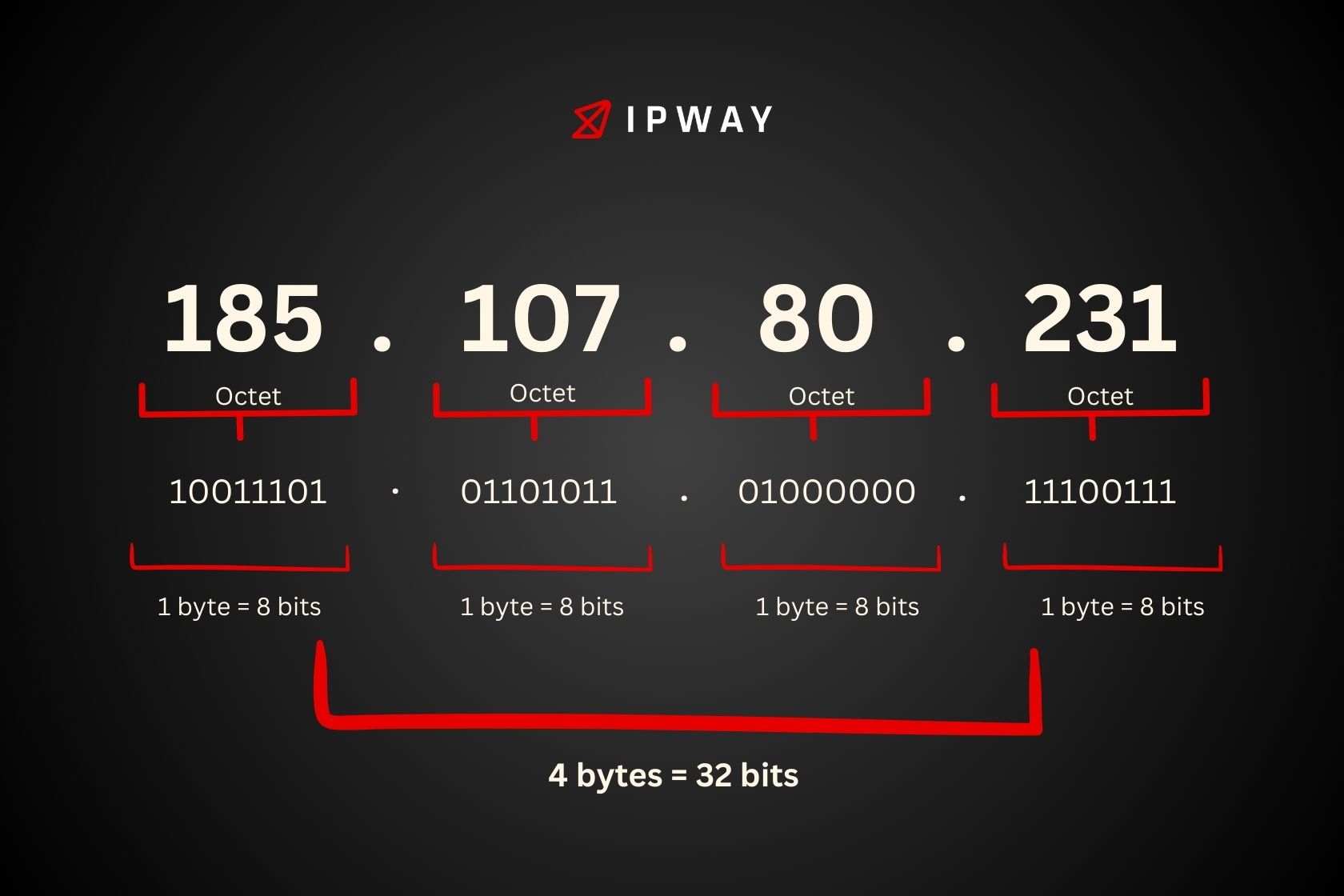
An IPv4 address is a 32 bit number given to every device linked to a network using the Internet Protocol for communication. Its usually shown in dot form making it simpler for people to read and grasp.
Dot-decimal Notation: The 32 bit address is split into four 8 bit sections with each section being separated by a dot. Each section is shown as a number from 0, to 255. For instance the IPv4 address 192.168.1.1 contains the numbers 192, 168 1 and 1 in its sections.
Binary Representation: Internally, IPv4 addresses are handled as binary numbers. Each octet in the dot-decimal notation corresponds to an 8-bit binary number. For instance, the address 192.168.1.1 translates to 11000000.10101000.00000001.00000001 in binary form.
Hierarchical Structure: The structure of IPv4 addresses allows for a hierarchical allocation of addresses. This hierarchy includes:
- Network Portion: The initial part of the address that identifies the specific network to which the device belongs.
- Host Portion: The remaining part of the address that identifies the specific device within that network.
Role of Subnet Masks in Address Allocation
Subnet masks play a role, in IPv4 addressing by dividing large networks into smaller more organized sub networks or subnets. This division improves network efficiency, security and structure.
Definition of Subnet Mask: A subnet mask is a 32 bit code that separates an IP address into two parts; the network section and the host section. It consists of a series of bits set to either 1 (, for the network part) or 0 (for the host part).
Example of Subnet Mask: For example when you see the subnet mask 255.255.255.0 written as 11111111.11111111.11111111.00000000 in binary it means that the initial 24 bits of the IP address represent the network part while the last 8 bits stand, for the host part.
CIDR Notation: Classless Inter-Domain Routing (CIDR) is a method used to specify IP addresses and their associated routing prefix. CIDR notation combines the IP address with the number of bits in the subnet mask. For example, 192.168.1.0/24 indicates an IP address with a subnet mask where the first 24 bits are the network portion.
Subnetting: When subnetting you split a network into smaller subnets by borrowing bits from the host portion to make more network bits. This results in subnets but fewer hosts per subnet. For instance applying a subnet mask of 255.255.255.128 (/25) on a network, with the base address 192.168.1.0 would give you two subnets; 192.168.1.0/25 and 192.168.1.128/25.
Address Classes and Private IP Ranges
Different classes categorize IPv4 addresses, each with functions for various network sizes. Private IP addresses have designated ranges for private networks and are not accessible, on the public internet.
Address Classes: IPv4 addresses are divided into five classes (A, B, C, D, and E) based on their initial bits. The first three classes (A, B, and C) are used for host addressing:
Class A: Large networks are capable of accommodating devices. The initial octet falls within the range of 1 to 126 allowing for a quantity of hosts per network, such as, in the case of 10.0.0.0/8 subnet.
Class B: Suitable for networks of size. The initial octet falls within the range of 128 to 191 accommodating an amount of hosts (, for example 172.16.0.0/12).
Class C: Best for networks. The initial octet falls within the range of 192 to 223 providing a number of hosts (, for example 192.168.0.0/16).
Private IP Ranges: Certain IP address ranges are reserved for private networks and are not routable on the public internet. These include:
- 10.0.0.0 to 10.255.255.255 (Class A)
- 172.16.0.0 to 172.31.255.255 (Class B)
- 192.168.0.0 to 192.168.255.255 (Class C)
These ranges are frequently utilized in households, workplaces and corporate networks to allocate IP addresses within the internal network while preserving public IP addresses.
It’s crucial, for network design, management and troubleshooting to grasp how IPv4 addresses are organized and the importance of subnet masks. When network administrators use these elements well they can establish adaptable and safe network setups.
IPv4 Functioning
IPv4 plays a role in todays networking landscape managing essential tasks to guarantee smooth and dependable data transmission, across networks. Lets delve into these functions in more depth:
Fragmentation
Fragmentation plays a role in IPv4 by dividing large data packets into smaller fragments to match the networks Maximum Transmission Unit (MTU). This division ensures packet transmission across networks with different MTU sizes preventing them from being rejected due, to size constraints.
- Process of Fragmentation: When a data packet is too large for a networks Maximum Transmission Unit (MTU) the sending host breaks it down into pieces each, with its own header. These smaller fragments are then sent individually.
- Reassembly: After the broken pieces arrive at their stop the recipient host puts them back together to form the complete package. The IP header contains details to guarantee that the fragments are reassembled accurately.
- Identification and Flags: The IP headers identification field distinguishes fragments of the packet while the flags and offset fields signify if a fragment is the final one and its location, within the original packet.
Service Handling
IPv4 includes features to manage services making sure that different kinds of traffic receive appropriate treatment based on their priority and needs. This is mainly done through the Type of Service (ToS) field, in the IPv4 header.
- Type of Service (ToS) Field: The Terms of Service (ToS) section enables users to set priority levels for types of data traffic. For example important real time services such, as voice and video can be prioritized over data traffic to reduce delays and maintain smooth communication.
- Quality of Service (QoS): Although IPv4s quality of service features are not as advanced as those in protocols such, as IPv6 it still offers simple methods to give priority to important data guaranteeing dependable transmission and efficient operation.
Routing
Routing involves guiding data packets from where they start to where they need to go through networks that are connected. The functioning of IPv4 depends on routers and specific protocols for routing to figure out the optimal route, for sending packets.
- Routing Tables: Routers keep track of routing tables that contain details, about the routes data packets can follow to reach their intended destination. These tables are regularly refreshed to match the layout of the network.
- Routing Protocols: IPv4 accommodates routing protocols, each with distinct algorithms and methods, for finding the best routes. Some popular protocols are:
Open Shortest Path First (OSPF): A routing protocol based on link state that employs a path first algorithm to determine the optimal route.
Border Gateway Protocol (BGP): A routing protocol commonly utilized for directing traffic between autonomous systems, on the web.
Routing Information Protocol (RIP): A distance-vector protocol that uses hop count as a routing metric.
- Path Determination: Routing protocols share data among routers to find the routes considering things, like network traffic, connection stability and rules set by network administrators.
Network Address Translation (NAT)
Network Address Translation (NAT) is a method utilized to link private IP addresses within a local network to one public IP address. NAT aids, in preserving the pool of accessible IPv4 addresses and boosts security by concealing internal IP addresses from outside networks.
Types of NAT
- Static NAT: Associates one IP address, with one public IP address. This method is commonly employed for devices requiring external connectivity like servers.
- Dynamic NAT: Assigns an IP address to a public IP address selected from a pool of available addresses. This method is commonly employed for establishing connections originating from, within a network.
- Port Address Translation (PAT): PAT, also referred to as NAT overload involves linking private IP addresses to one public IP address while differentiating connections, by port numbers. This setup enables devices to utilize a single public IP address at the same time.
Security Benefits: NAT improves network security by concealing IP addresses from outside sources, which adds an extra layer of protection, against potential attackers trying to pinpoint individual devices within a private network.
Benefits of Using IPv4
With the rise of IPv6 IPv4 still stands as the predominant Internet Protocol thanks to numerous advantages that have solidified its place in the foundation of the internet. It’s essential to grasp these benefits to comprehend why IPv4 has remained prevalent and significant, over time. In the following section we delve into the advantages of utilizing IPv4:
Simplicity and Familiarity
Widespread Adoption: Since the inception of the internet IPv4 has been widely utilized, making it prevalent, in network configurations ranging from personal home networks to corporate settings. This widespread usage has led to all networking equipment, programs and infrastructures being tailored to accommodate IPv4 guaranteeing smooth compatibility.
Ease of Understanding: The format of IPv4 addresses is simple and clear for individuals who are new to networking. The used dot decimal notation (for example 192.168.0.1) is user friendly enabling network administrators to efficiently oversee and resolve network issues without the need, for specialized expertise.
Mature Ecosystem: Throughout the years a wide range of tools, software and proven methods have developed around IPv4. Network administrators can tap into resources to set up oversee and protect IPv4 networks. This level of advancement ensures that solutions are readily available, for any networking issue that may come up.
Compatibility and Integration
Legacy Systems Support: Numerous older systems and devices in operation were originally tailored for IPv4. It is essential for many companies to maintain compatibility with these systems and IPv4 offers a smooth transition to incorporate both new and old technologies without the need, for significant alterations.
Broad Compatibility: The ranging compatibility of IPv4, on different platforms and devices makes it easy to integrate and expand networks. Whether you’re connecting devices or combining networks IPv4s support reduces potential problems and simplifies the setup.
Cost-Effectiveness
Infrastructure Costs: Many companies face expenses when switching to IPv6 due, to the need to upgrade or replace their current infrastructure. By sticking with IPv4 these organizations can delay these costs. Maintain their existing network equipment and setups.
Operational Efficiency: IT experts are well versed in IPv4 networks, which helps cut down on the necessity for training or hiring new employees. This existing knowledge results, in improved efficiency and reduced costs associated with network management.
Robustness and Reliability
Proven Track Record: IPv4 has established itself as an stable option. It has been extensively. Refined over many years of practical application making it a strong choice, for networking purposes.
Extensive Troubleshooting Knowledge: With its background IPv4 networks have a wealth of information and resources for troubleshooting and problem solving. This rich source of data enables network administrators to promptly pinpoint and resolve issues reducing any disruptions, in operations.
Addressing Flexibility
Private Addressing: Private addressing schemes in IPv4 make it possible for organizations to establish internal networks without using up public IP addresses. This feature is especially advantageous, for companies and data centers.
Network Address Translation (NAT): NAT allows several devices within a network to utilize one public IP address helping save public IP address resources. This feature plays a role, in addressing the problem of IPv4 address depletion and promotes the effective utilization of the existing address pool.
Scalability
Hierarchical Addressing: The structured layout of IPv4 addresses supports the scalability of network design. Through subnetting companies can effectively manage address allocation improve routing and boost network efficiency.
Variable Length Subnet Masking (VLSM): VLSM permits an adaptable and effective utilization of IP address space by allowing the formation of subnets, in different sizes. This flexibility assists companies in optimizing their address assignment based on requirements ultimately improving scalability.
In summary the advantages of utilizing IPv4. Its ease of use, adaptability, affordability, reliability, address flexibility, scalability, security aspects and consistency. Clarify why it still stands as the protocol in current use. With the increasing integration of IPv6 the well established framework and broad backing of IPv4 persist in making it an essential element, in contemporary networking.
IPv4 Security
Even though IPv4 is commonly used it was not initially created with security measures leaving it open, to different types of attacks. Fortunately various security protocols and enhancements have been introduced to bolster its defenses. Here’s a brief summary outlining the security elements and obstacles associated with IPv4:
Basic Security Challenges of IPv4
Lack of Inherent Security: IPv4 does not come with built in encryption and authentication which leaves it vulnerable to attacks such as spoofing, sniffing and man, in the middle interceptions.
Address Spoofing: Attackers have the ability to manipulate IP addresses in order to conceal the origin of traffic making it harder to track.
Fragmentation Attacks: Flawed or intersecting parts can be manipulated to circumvent security protocols.
Best Practices for IPv4 Security
Regular Updates: Remember to update your devices and software to fix any potential security weaknesses.
Strong Authentication: Implement multi-factor authentication.
Network Segmentation: Separate the network into sections to prevent possible security breaches.
Continuous Monitoring: Monitor traffic and logs for suspicious activity.
Incident Response Plan: Have a plan to quickly address security incidents.
Conclusion
IPv4 has served as the foundation of internet communication for years offering a strong and dependable method for linking devices worldwide. Despite its constraints, IPv4 remains prevalent due to its widespread acceptance. Knowing the ins and outs of IPv4 including its functionality, advantages and obstacles is essential for individuals engaged in networking and IT. While the global shift towards IPv6 progresses IPv4 retains its position, as an element of our digital framework.
Become a part of the IPWAY network and benefit from automated IP leasing with unparalleled convenience.
